Red Teams. Blue Teams. “Mix” them together and it’s a Purple Team.
If at least Blue Team operations have reached a certain level of maturity, then the company may be ready for a Purple Team assessment. Purple teaming is a type of assessment comprised of a mutually beneficial process for the attackers and defenders.
Purple Team(ing) is a concept as old as cyber Red and Blue teams but the term is still young, having only been around for about five years. The term itself may denote a third team in parallel to the Red and Blue, but it is a process life cycle generated when both teams benefit from the offensive and defensive activities.
Needing a Purple Team Assessment
The need for a Purple Team materializes only after the Blue and/or Red Team (if the RT is internal) capabilities and operations have reached a certain level of maturity within the organization. Or, in the case where the blue functions are outsourced to a third party (keep in mind the 3rd party MSSP may have no interest in this type of engagement).
View a Purple Team, and its assessments, as an outgrowth of collaboration between the various offensive and defensive capabilities and operations of the organization. If the organization has no offensive or defensive operations, then the need for a Purple Team does not exist.
If the organization only has defensive capabilities, then bringing in an outside Red Team to participate in a Purple Team engagement may still be an option, but again, this option should only get consideration when the defensive operations and capabilities are developed.
What is a Red Team?
A Red Team is the group who emulates specific or generic tactics, techniques, and procedures (TTPs) of an adversary, with the objective of assessing the organization’s cyber security assumptions. The assumption could range from statements like “That would never happen because of X” to “We just installed Y and we think it’s working.“
An example use case for a Red Team: an organization just spent a lot of money to protect a couple core databases critical to the revenue stream of the company. Now the company wants to know if the processes and controls are working as intended.
There are many similarities to a penetration test, however a penetration test does not care about any assumptions or adversary TTPs, the penetration test cares about what it able to do given the scope and rules of engagement. Penetration testing is the catch-as-catch-can of security assessments, where the Red Team is the sparring partner trying to fight like the upcoming opponent.
What is a Blue Team?
The Blue Team, at a minimum, is the operational opposition to any adversary bent on destroying or diminishing the IT functions or data of the organization. The Blue Team watches the alerts, takes actions on the alerts, helps improve detection and response capabilities of tools, responds to incidents and hunts for adversaries on the network.
The Blue Team is often broken into various functional teams like security analysis in the security operations center, incident responders on the cyber security incident response team, and threat hunters on the threat hunting team.
These teams normally have a process flow that allows alerts and activates to move around from one team to the other as part of integrated operations.
What is a Purple Team?
A Purple team is the life cycle that is created when the Red and Blue Teams come together and form processes around the objective of improving each other’s tools, techniques, and procedures.
The Red Team attacks and the Blue Team defends. There is a process of collaboration and communication between the two teams during and after activities.
This collaboration allows for both teams to improve.
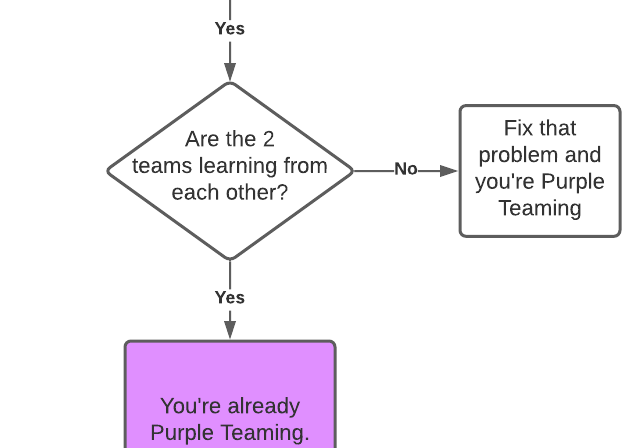
On a philosophical note, if an organization has both Red and Blue Teams, Purple Teaming is a matter of getting the two teams to play together for each other’s benefit. It’s not bringing in a third team, that’s called therapy.
For example, if the Red Team was able to reach their objective undetected or uninhibited, the Red Teamers might say something like “We did X on system Y at time Z” and the Blue Team will search through logs and alerts trying to figure out what “went wrong” – if an alert didn’t fire, why? If it did, why wasn’t it seen? What clues exist on the network that can get converted into new alert triggers? etc.
In turn, if the Red Team was detected or prevented from reaching the objective the Blue Team can provide similar feedback, “We detected you running X command because it was a child process of something we alert on.” Then with that information the Red Team can work out how to not get caught, updating TTPs.
If an organization has no Red Team and wants a 3rd-Party Purple Team, that organization is really looking for an external Red Team who is willing to play nice and “talk shop” so they can benefit from more than just a vulnerability report. Don’t get sucked into marketing hype.
When to use a Purple Team
If the organization has both a Red and Blue Team and they play well together to improve each other’s TTPS… the organization has a Purple Team. That’s not to say process don’t need better development but all the titles, processes, and procedures in the world won’t make a Purple Team if the Red Team is out to make the Blue Team look ridiculous or the Blue Team trusts the Red Team like parents trust a scorpion to watch their children.
If the organization has a Blue Team but no Red Team and the organization wants to Purple Team, then here is a checklist to determine if your organization is ready:
- Does the organization have a bassline level of security controls? If the organization does not have the below bassline, there is almost no benefit is the purple team as an activity and given the cost of such an engagement, it’s definitely not worth it.
- Asset management
- Data Backups
- Phishing countermeasures
- Patch and Vulnerability Management
- Endpoint Detection and Response (EDR, not antivirus)
- Secure configurations
- Multifactor Authentication
- Has the organization implemented a cyber security framework like NIST or CIS 18? A cyber framework is not security (it does define and manage risk) however the implementation of a framework can provide additional foundation on top of the baseline to build a defense-in-depth.
- Does the organization have a functioning security operations center and/or cybersecurity incident response team?
- Does the SOC/CSIRT have documented processes? This is more than an incident response plan. These processes should describe the various tools, techniques, steps, etc. should use and follow given a variety of scenarios.
- Does the organization have regular penetration tests and/or red team assessments?
If your organization can answer “yes” to all of those questions, then a purple team assessment is a viable next step. Here is a simple decision tree to help.

The reality is most businesses (given millions of small businesses make up the majority of businesses) will never need a purple team assessment.