Compliance is important given the potential financial weight resulting from incompliance, however it is important to understand the difference between security compliant and being secure.
Cyber compliance does not mean the business is secure. Compliance is better than nothing, but equating compliance to security results in an overconfidence in the company’s actual security defenses.
The confusion often arises when a business treats the compliance audit as a security assessment. Which, as one might have guessed already, a cyber security audit to measure compliance is not the same thing as a cyber security assessment to measure cyber security.
Cyber Compliant Does Not Mean Cyber Security
Does compliance mean anything? Yes. A positive state of compliance means a reduction in liability: no fines (or worse depending on the industry) for incompliance and lower, to no fines, because of a breach.
Compliance is not security, it’s liability management. This is not a bad thing. Money going out the door because of fines is no different than money going out the door due to a data breach and resulting recovery – given the company survives. Money lost is money not spent on employee raises, product expansion, marketing, etc.
Compliance is a state of validation against a set of government and/or industry requirements. Meet those requirements to an auditor’s satisfaction and the company is considered compliant. Fall short just enough and the company is out of compliance.
Usually, the company has a period of time to meet the requirements and get reaudited or fines begin to add up. From a business perspective – avoiding these fines is the real goal of compliance, not security. Even if security (data protection) is the reason the requirements exist in the first place (from a policy perspective).
It might seem like a paradox, yes, but that is what happens when policy meets reality.
Compliance means a reduction in liability.
So, if compliance is not security, and a company wants to know if they are secure, then how do they go about finding out?
How to Know How if the Business is Secure from Cyber Attack?
The only way to know if a business is secure from a cyber-attack is to fake an attack and see what happens. These fake attacks are called penetration test and red team assessments.
Understand, this is not the same question as “Does my business have any vulnerabilities?”, because the answer is: Yes, of course. This matters because attackers don’t stop after detecting the vulnerability. Attackers exploit it and then use the new access to carry on further attacks until an objective is achieved.
A vulnerability scanner will work fine for answering “Does my business have any vulnerabilities?”, but a vulnerability scanner can’t say if the business is secure from a cyber-attack.
Cyber security is a measurement (or a diagnostic depending on how one looks at it). A business is more, or less, secure, depending on the capability of the controls put in place to protect the business’s operations and data from a cyber-attack. A penetration test and/or red team engagement measure the effectiveness of these controls.
Brief Pentest & Red Team Comparison Interlude
There are important distinctions between penetration testing and red teaming assessments – and other types of security assessment. Explore some of these difference in Alternatives to Penetration Testing and Do I need a Purple Team Assessment?
Suffice it to say, the key distinction between pentesting and red teaming relevant to the question how secure is the business? is one of breadth and depth. Where a penetest tends to focus on pure technical activities, red teaming extends to multiple layers of relevant technical, operational, and organizational elements of the business.
Breaking the main question down into a few sub questions may help illustrate the distinction.
| Is the business secure from a cyber-attack: “sub questions” | PT | RT |
| Can an Attacker get on the company network? | X | X |
| What can an Attacker access? | X | X |
| What are the various ways the technology is not secure from an Attack? | X | |
| What can an Attacker steal? | X | X |
| What kinds of Attackers should concern the business? | X | |
| Will the business continuity plan work? | X | |
| Do people “know” what to do during an attack? | X |
On a financial note: the more Xs covered in an assessment, the more a company will know about its security and the more money they will pay to know it.
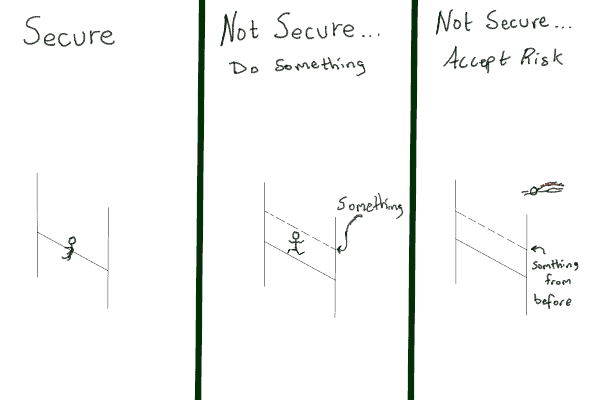
Nothing is totally secure. Complete security is not possible in the same way actual light speed travel is not possible. Complete security would require all available funds – which just means the business secures itself out of existence. [Light speed travel requires infinite energy].
Since achieving total security is not possible, then the goal becomes something more reasonable: just enough security. Just enough security is when all legitimate threats to the business operations and data are taken into consideration and mitigated (or ignored) to an acceptable level of risk.
The threats plus risk acceptance becomes the internal standard for measuring the security of the organization. Threats will take advantage of vulnerabilities, misconfigurations, unwitting employees, or whatever else to gain access and achieve their goal. However, at some point, since a business can’t prevent everything, it must accept certain risks.
At some point the business has done something to secure against attacks, then the business wants to how hard it is to jump over that something. A pentest (or red team engagement) is conducted (SMBs should engage a 3rd-party vendor) and the results are measured against the threats and the acceptable risks.

The internet is a hostile place. Doing business on the internet – even if it’s just business data stored in the internet – means exposure to a myriad of threats less than savory. For years business ignored security to the detriment of their customers, so governments and industry players stepped in and imposed regulations under the penalty of heavy fines and/or prison.
The fear of fines will only make business do just enough to avoid the fines. And that just enough to avoid fines does not mean the business is secure from an actual cyber threat… but it could if the business followed the letter and the spirit of the regulation.
The only way to know is to do a security assessment (not a compliance audit).